PROTECT YOUR BRAND PLAY OFFENSE AGAINST FRAUD
Find and destroy account takeover, identity theft, and credit card fraud scams upstream — before your customers become victims.
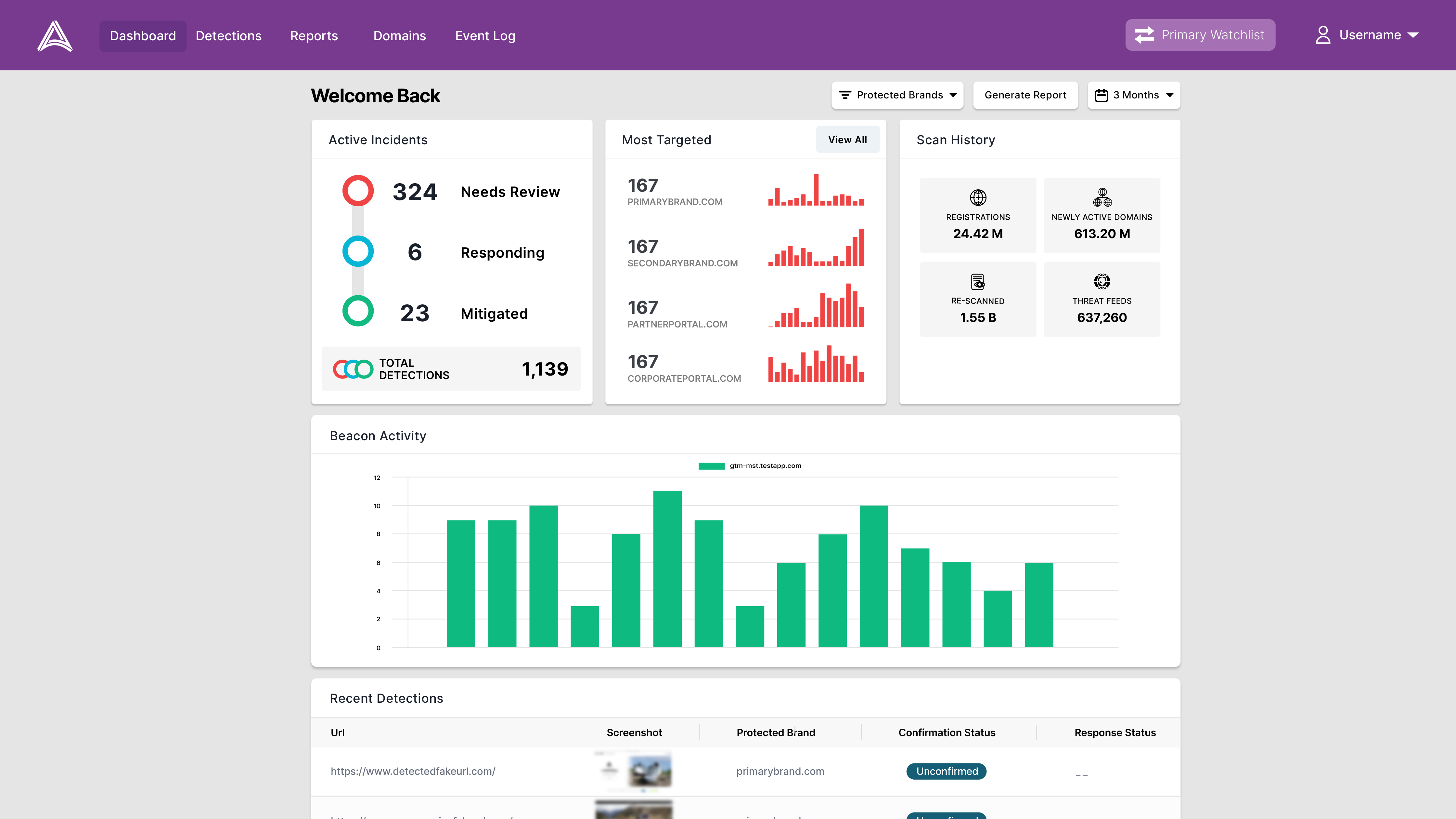
THE DATA MATTERS
Prevent brand abuse on the web, social media platforms, and mobile app stores via site takedown, trademark enforcement, and DMCA enforcement

WHAT OUR CUSTOMERS ARE SAYING
CUSTOMERS SHOULDN’T BE YOUR DETECTION METHOD
Traditional methods largely rely on victims to report online scams by calling customer service with a problem. By then it’s too late. Allure Security’s AI finds the attacks others miss. Powered by computer vision and natural language processing, we search millions of sites to spot online impersonations of your brand before victims do.
AUTOMATICALLY IDENTIFY ONLINE IMPERSONATIONS
Allure Security uses sophisticated AI to comb through millions of online sources to find copycat domains, rogue websites, phishing attacks, fake social media profiles, and other scams – without any manual effort.
STOP SCAMS IN THEIR TRACKS
Allure Security’s extensive network of security partners allows us to block victim access to attacks from over 95% of internet connected devices world-wide within minutes.
TAKEDOWNS AND TRADEMARK ENFORCEMENT
Allure Security’s team of experts manage the entire process of executing takedowns for our customers. Any type of brand impersonation, operating on nearly any platform, anywhere in the world. Allure Security will work to clean it up and enforce your digital rights.
ALLURE PROTECTS CUSTOMERS IN ANY INDUSTRY
Now your customers can go about their business feeling safe
FINANCIAL SERVICES
Banks, Crypto Wallets, Payment Providers, Broker/Dealers, Financial Advisors, Asset Managers, FinTechs, Accountants, Insurance Companies and Credit Unions are lucrative targets for fraudsters. After all, Finance is where the money is. Banks and Credits Unions are especially targeted, read our 2022 Threat Brief to learn more.
ECOMMERCE
Online merchants of all types are a top target. Payment card data, loyalty program points, and sensitive personal information are currency for fraudsters. Online merchants are active in social networks, blogs and may appear in advertisements almost anywhere – giving the scammers endless options to find victims.
DIGITAL PUBLISHERS
Digital publishers generate revenue from advertising and subscriptions. Fraudsters scrape and re-publish original content to siphon-off a publisher’s ad revenue. They impersonate the subscription and pay flows to steal credit card data. With massive user-bases, media companies are a top target.
GOVERNMENT
As Government business increasingly moves online, scammers have followed. Electronic Taxes, Online Postage, Voter Registration, Disaster Relief, Public Surveys, and more provide fertile ground for fraudsters to operate. Government has emerged as a top target since the COVID crisis began in early 2020.
HEALTHCARE
Healthcare organizations, on both the payer and provider side hold very sensitive patient information that when exposed can lead to identity fraud. The growth of the use of debit cards for Medicare programs can make health insurers look a lot like banks to a criminal. Healthcare is an emerging target for online fraud.
HIGHER EDUCATION
Educational institutions have long been a popular target for cyber scams. Despite efforts to protect faculty and students, online enrollment and payment processes remain exposed and vulnerable – as do many prized university resources, such as private research libraries. Fraudsters have set their sites on schools as these resources can be easily monetized.
LEARN MORE ABOUT HOW WE PROTECT YOUR CUSTOMERS
We’re here to answer any questions you have about how we prevent brand abuse on the web, social media platforms, and mobile app stores via site takedown, trademark enforcement, and DMCA enforcement.



