The phishing scheme aimed at top YouTube content creators is a real-time case study in how these attacks are evolving and becoming more sophisticated. It also underscores that the current “damage control” response by companies is unproductive and smacks of victim blaming.
Here’s what we know so far. The attackers used highly targeted phishing techniques to convince YouTube account owners to give up their Google account login credentials, and used that information to enter the accounts, change their vanity URLs and then re-assign them to new owners. The actual owner of the channel and its subscribers are left thinking the account has been deleted. The attackers were also able to bypass Google’s two-factor authentication required for each account, possibly by using a tool called Modlishka to intercept text messages containing the security codes.
In the aftermath of disclosing this attack, Google, the parent company of YouTube, has gone down a familiar public-facing path in its public response. The first move is to downplay the severity and pervasiveness of the attack, pushing back against the estimated number of users (23 million, by some reports) who could be affected by it. In the company’s official response to the breach, YouTube’s statement read:
“We have not seen evidence of an increase in hacking attempts over the weekend. We take account security very seriously and regularly notify users when we detect suspicious activity. We encourage users to enable two-factor authentication as part of Google’s account Security Checkup, which decreases the risk of hacking.”
The second move in the damage control playbook is to continue to position 2FA as a line of defense against phishing. But this case clearly shows that it can easily be bypassed without the user- and the targeted company- even realizing it.
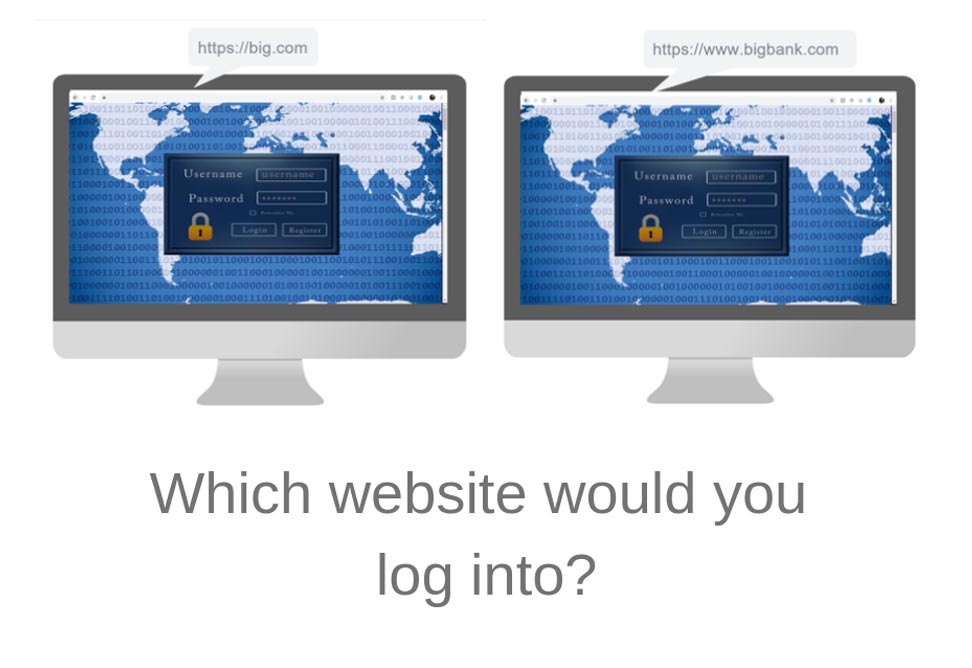
The problem with Google and YouTube’s response to this breach is that it doesn’t take into account how today’s phishing emails and spoofed websites are genuine at first glance, even to the trained eye. And it’s important to remember that users aren’t trained to spot spoofed websites, nor should it be their responsibility to detect this on behalf of the company. Due to the pervasiveness of web spoofing attacks, companies should be in charge of defending their websites from phishing and spoofing to protect their customers’ personal data, not just their employees.
The attackers in this case showed remarkable ingenuity and effective success. It doesn’t take much technical skill to orchestrate an attack like this – most of the tools can be bought fairly cheaply on the dark web. Perhaps instead of being reactive and engaging in the familiar damage control playbook, companies should match the savviness of their adversaries with their own ingenuity and effective active defense.
Here’s how defenders can stop phishing and web spoofing before millions of customers are duped into giving up their credentials:
- Aggressively searching for spoofed sites, using embedded Beacons that serve as “GPS” trackers. These bits of code alert security teams when an adversary has copied a webpage and used it for spoofing purposes, such as a bank’s login page.
- Once detected, contact your ISP and request an immediate takedown of the spoof URLs.
- Gather information on which and how many customers have been victimized, and immediately reset passwords while the ISP takedown is attempted.
- Actively defending the credentials belonging to customers by poisoning the attacker’s cache of victim credentials using decoy credentials. This will fill the adversary with doubt that they have captured anything of real value.
The YouTube attack demonstrates that phishing and web spoofing aren’t going away any time soon; if anything, this type of attack is increasing. Customers shouldn’t be held responsible for advanced threats, or for detecting phishing campaigns. It should be the responsibility of the targeted company to actively defend itself and its customers.
Find out more about how Allure’s approach helps organizations detect phishing schemes and web spoofing faster. Get in touch today.