The number of brand impersonation attacks using unique scam websites hit an all-time high in December 2021 – more than tripling compared to early 2020. That’s according to the Anti-Phishing Working Group – a consortium of vendors, government agencies, and more – that has tracked trends in phishing and identity theft for 18 years.1 Fraudsters wouldn’t continue to spend time creating fake websites that impersonate trusted brands if they didn’t succeed in fooling consumers and bringing in revenue. Taking a look at the data can help businesses understand reasons why criminals might target their brand and help businesses know where to look to find and eliminate fake websites abusing their brand. With this article, we provide some commentary on the report and augment the data with a few insights from Allure Security’s AI-based detection engine that analyzes more than 50 million websites a day to detect thousands of brand impersonations.
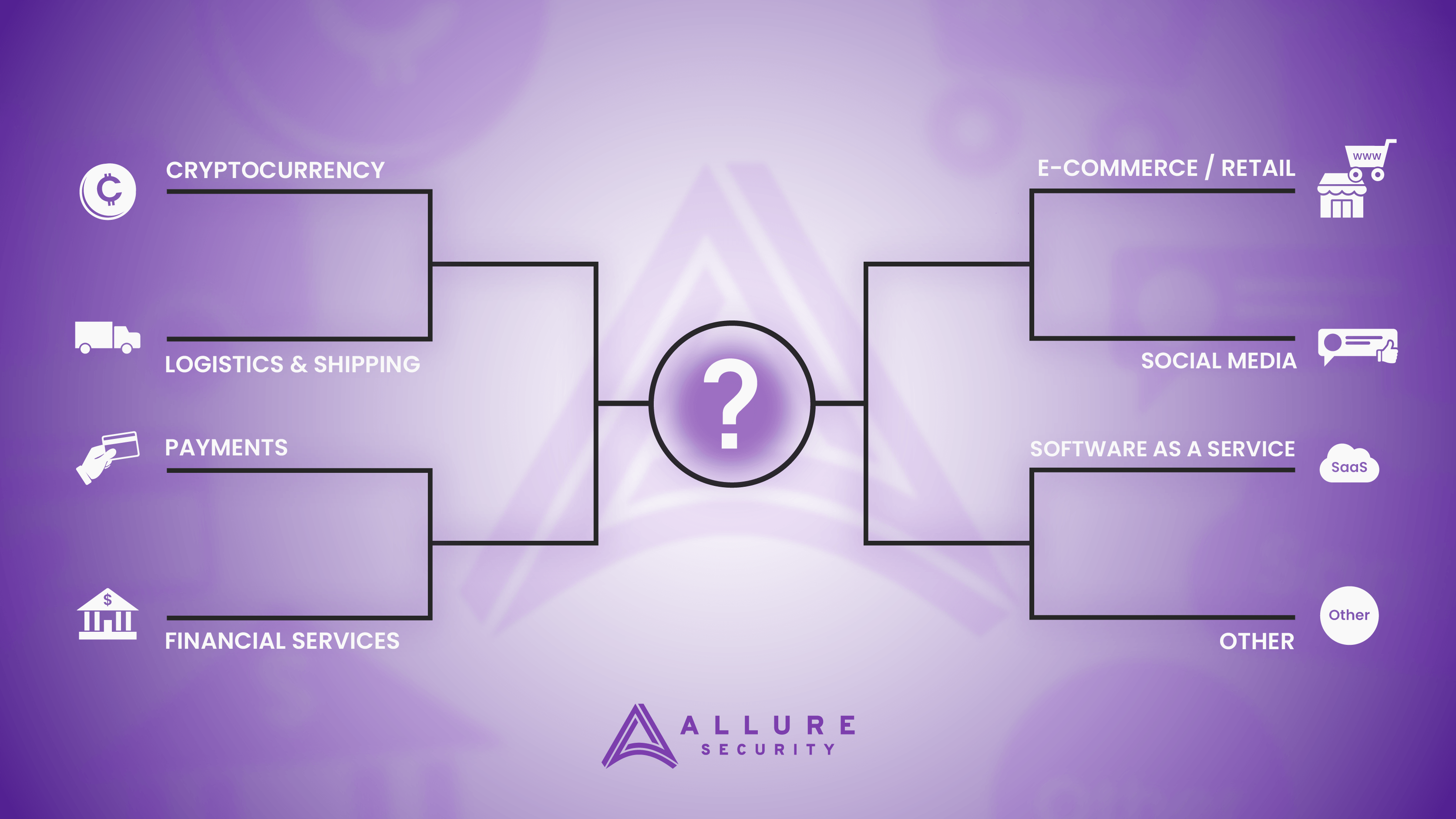
Brand Impersonation Attacks: Most Targeted Industries Q4 2021
- Financial Services – 23.2%
- SaaS/Webmail – 19.5%
- E-Commerce/Retail – 17.3%
- Payments – 9.3%
- Social Media – 8.5%
- Cryptocurrency – 6.5%
- Logistics/Shipping – 4.1%
- Other 11.6%
Financial Services
Fraudsters typically target financial services with brand impersonation attacks in an effort to steal banking credentials. If a bad actor can trick an account-holder into divulging their username and password for online banking, as you might imagine, they can then drain that account. It can be the quickest route to revenue. Keep in mind that fraudsters don’t only target large household names. We regularly find numerous impersonations of smaller financial institutions. This shows that assuming your financial services brand is too small for attackers to take notice leaves your brand and your customers exposed.
SaaS/Webmail
Attackers highly value e-mail account credentials. Controlling a person’s e-mail account can be a skeleton key to a number of accounts owned by the unlucky victim. Many password reset methods involve sending password reset and other notifications and links to people’s e-mail accounts. If an attacker can compromise a user’s email address and has reason to believe that person also holds an account at a particular institution, an attacker may only be a “Forgot password?” link away from owning that bank account.
In addition, taking over an e-mail account to then impersonate that account holder and trick their contacts (many times stored within those e-mail accounts), can bear fruit for an attacker to scam more people out of their money, personally identifiable information and more.
E-commerce/Retail
The Federal Trade Commission reports that online shopping fraud losses in the U.S. increased 56% to $392.4 million in 2021 over 2020.2 In the past, the FBI has estimated that counterfeit goods cost the U.S. economy $600 billion annually.3 Crooks generally launch brand impersonation attacks against e-commerce and retail brands to steal credit cards, peddle counterfeit goods, sell goods procured via illegitimate means (stolen merchandise), or to facilitate non-delivery fraud. Non-delivery fraud consists of a scammer spoofing a well-known retailer, collecting a consumer’s personally identifiable information and payment details, and charging the person for goods that never arrive.
Some schemes go so far as to send a fake tracking number to the victim to buy the fraudster some time before the consumer notices that something is awry. The tracking number may be completely random and not in any way associated with the victim’s actual address or the shipment they expected.
Payments
Users appreciate real-time payments because they can pay someone in seconds without having to carry cash or pull out a payment card. Unfortunately, so do criminals. Because of the speed with which funds can leave your account, there’s less time to scrutinize the payment and so fraudsters can more easily make off with that money. Because many payment services execute transfers that are irreversible by the initiating bank, banks typically refuse to reimburse customers for fraud. The recent run of Zelle fraud is a well documented example.4
Other brand impersonation attacks that target payment brands include
- Scammers send “fraud alerts” allegedly from a digital payments service and then direct the recipient to a fake website impersonating the service’s brand including a spoofed log-in page that steals a user’s credentials that the attacker uses to drain the account
- Fraudsters publish malicious online ads that advertise a customer support number that has nothing to do with the payment service and instead directs a caller to the scammer who will collect account details and drain the account5
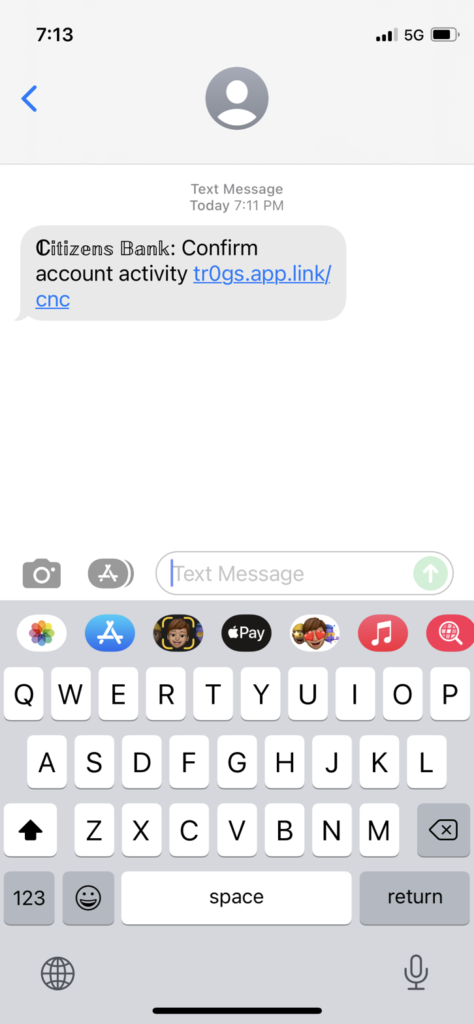
- An e-mail or SMS message disguised as a payment request or notification along with a malicious link directing the victim to a fake payment service log-in page that then steals the user’s credentials
Social Media
In addition to traditional phishing scams where a crook creates a fake website impersonating a social media platform in an effort to steal a user’s credentials, swindlers will also impersonate brands on social media. In particular as of late, we’re seeing an uptick in criminals impersonating sellers of investment products on social media.6 They may outright steal an investment advisor’s digital identity, pose as that investment professional on social media platforms, and then solicit money from potential investors.
In other cases, a con artist will create an identity and use an investment firm’s logo to appear credible and give the impression they’re registered with the Securities and Exchange Commission (SEC) and/or the Financial Industry Regulatory Authority (FINRA). In that case as well, the swindler will ask for money.
We’re also seeing more and more attackers posing as cryptocurrency-related brands on messaging channels via Telegram, What’sApp and others. Links to scam websites spoofing legitimate cryptocurrency brands proliferate more and more via these and other social media channels.
Cryptocurrency
Attackers continue to target cryptocurrency brands with scam websites and brand impersonations – 6.5% of scam websites identified by APWG in Q4 of 2021 were related to cryptocurrency. As more people get involved with cryptocurrency, so too do cybercriminals. Our AI-based brand impersonation engine tracks hundreds of cryptocurrency exchange brands and not a day goes by without another detection. In many cases, fake websites impersonating a cryptocurrency wallet or exchange hope to pilfer users’ credentials or passphrases in order to take over their account and transfer funds to an account controlled by an attacker.
The Allure Security detection engine and Threat Research Team has also spotted increasingly prevalent cryptocurrency-related scams that proliferate via Twitter and Google ads and ask the victim for their seed phrase or recovery phrase in order to log-in. This seed phrase is the master key to a cryptocurrency wallet. If a user is fooled into providing the phrase, the scammer can use it to steal the cryptocurrency associated with that wallet.
Logistics and Shipping
It’s estimated that worldwide e-commerce sales grew 16% to $4.9 trillion in sales in 2021 over 2020.7 That means there are more people in the world eagerly awaiting packages shipped to them by any number of package delivery services. Criminals take advantage of this anticipation, knowing more people are primed to visit a fake shipping website prompted by an urgent shipping notification.
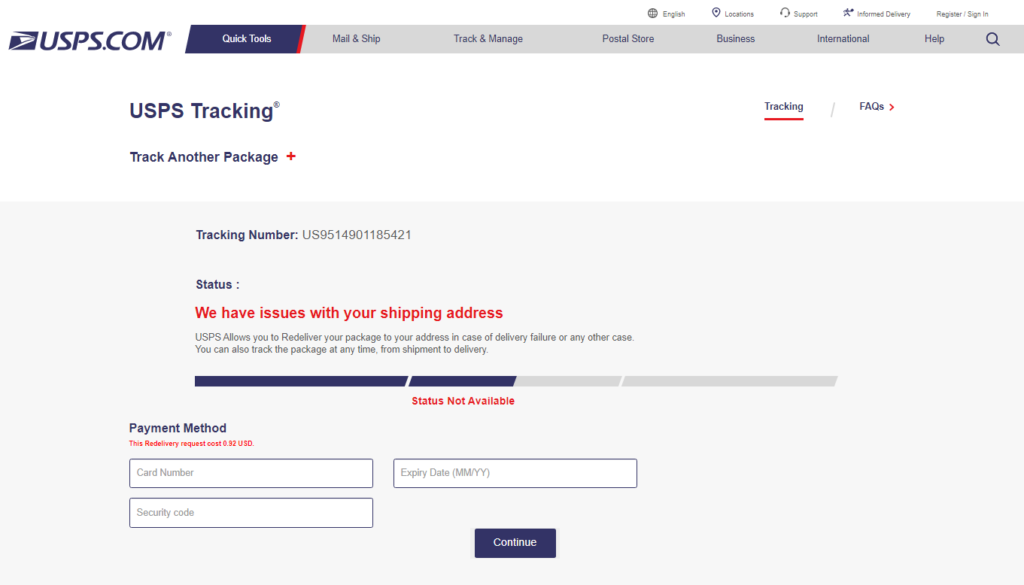
Many of these scams aim to persuade victims to provide payment details in order to expedite shipping, or, as in the United States Postal Service website brand impersonation attack pictured below, in order to reschedule a missed delivery.
Brand Impersonation Attacks & Online Scams of the Day
While for the most part brands in the financial services, e-commerce, retail, and payments industries will always hold a spot atop the list of scammers’ favorite targets, current events can occasionally affect the list. For example, the war in Ukraine has resulted in increased Allure Security detections of scams related to donating money to help displaced Ukrainians8 and may lead to an increase in brand impersonation attacks targeting government agencies or online charitable donation services.
If you take nothing else away from this article, just know that brand impersonations and fake websites affect brands of all sizes in all sorts of industries. Any brand that has built trust with their customers can bet on attackers trying to take advantage of that trust. The costs of brand impersonations and fake websites include, but are not limited to, direct fraud losses, lost sales, reputation damage, customer dissatisfaction, and decreased staff morale.
Regardless of your industry, stay up-to-date on scammers’ latest methods to ensure you’re sufficiently protecting your brand and customers — learn the basics of online brand protection with our Busy Person’s Guide to Online Brand Protection. For help getting a handle on how much these scams brand impersonation scams may be costing you, try our free brand impersonation scams cost calculator. Or, if you need more visibility into your digital risk in this area, Allure Security offers a free brand impersonation report.
1 https://docs.apwg.org/reports/apwg_trends_report_q4_2021.pdf
2 https://public.tableau.com/app/profile/federal.trade.commission/viz/FraudReports/FraudFacts
3 https://www.digitalcommerce360.com/2021/08/02/counterfeit-goods-online-the-government-acts-despite-platforms-efforts/
4 https://www.nytimes.com/2022/03/06/business/payments-fraud-zelle-banks.html
5 https://dfw.cbslocal.com/2021/02/11/beware-scammers-target-cash-app-zelle-venmo-paypal-users-for-fast-money/
6 https://www.sec.gov/oiea/investor-alerts-and-bulletins/fraudsters-posing-brokers-or-investment-advisers-investor-alert
7 https://www.statista.com/statistics/379046/worldwide-retail-e-commerce-sales/
8 https://www.cnet.com/news/war-in-ukraine-brings-out-scammers-trying-to-exploit-donations/